suSSHi Documentation
Welcome to the official online manual of the suSSHi Suite.
About suSSHi
suSSHi is your first solution for an unique entry point to data center and cloud resources. It enables you to control and log all SSH access to these resources. suSSHi provides simple configuration, manageable profiles and access rules for each and every target system.
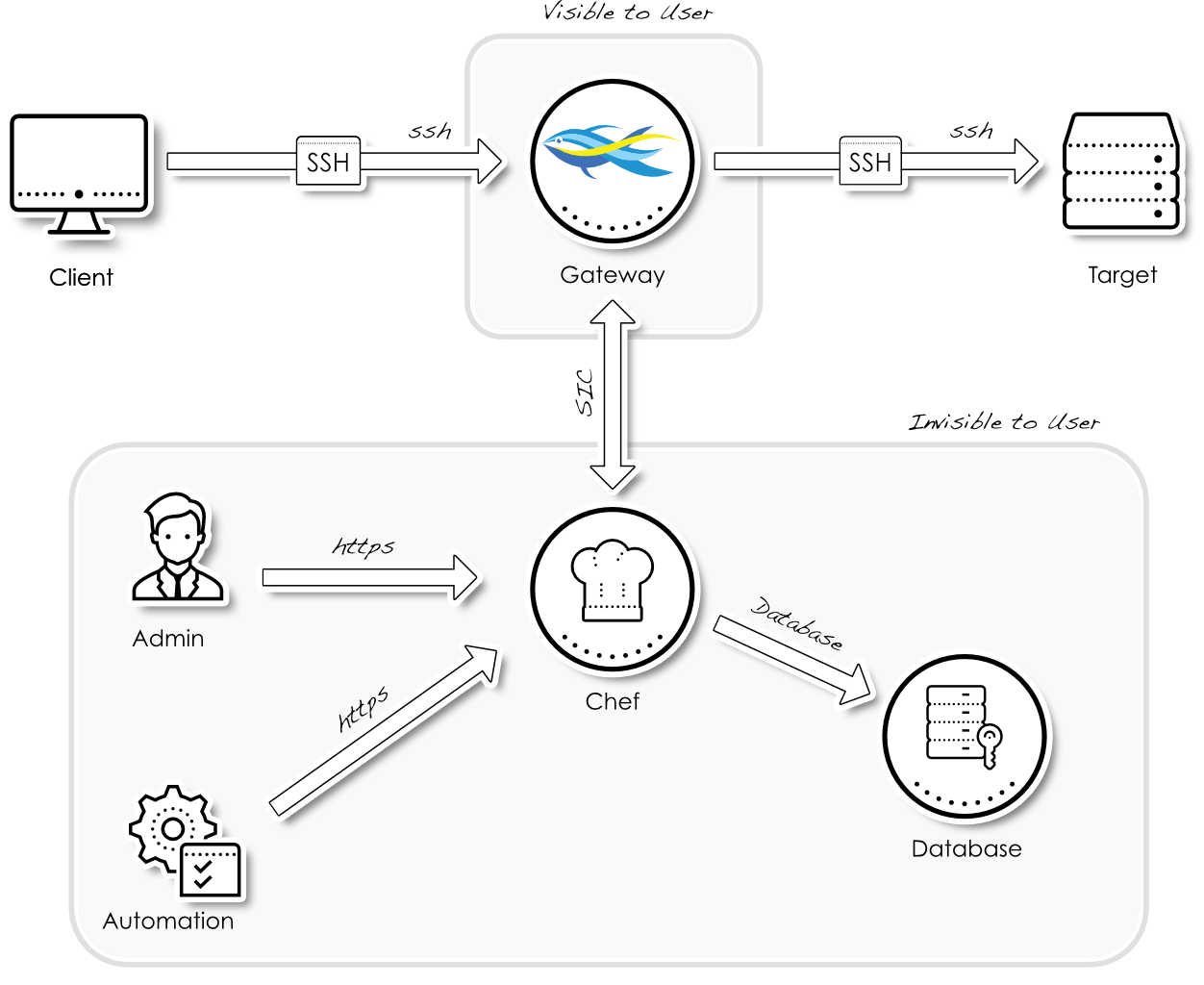
While some will call it a SSH gateway solution, we call suSSHi a multi-tool Swiss Army Knife, when it comes to authentication and authorization. On the client and on the target side, suSSHi supports Public Key authentication, Keyboard-Interactive and Password authentication. Depending on your business requirements, multiple combinations are possible.
What makes suSSHi a masterpiece in authentication is the full integration of all authentication dialogs within the SSH authentication phase. It simplifies client error handling and enables graphical SSH clients with authentication dialogs to display them correctly instead of showing prompts in the terminal session.
In addition, the authentication and authorization processes can be further customised by our professional service through a flexible plug-in architecture.
Chef Cuisine
suSSHi Chef is the central user account and access management of the suSSHi Suite. A modern user interface assists you in all administrative tasks.
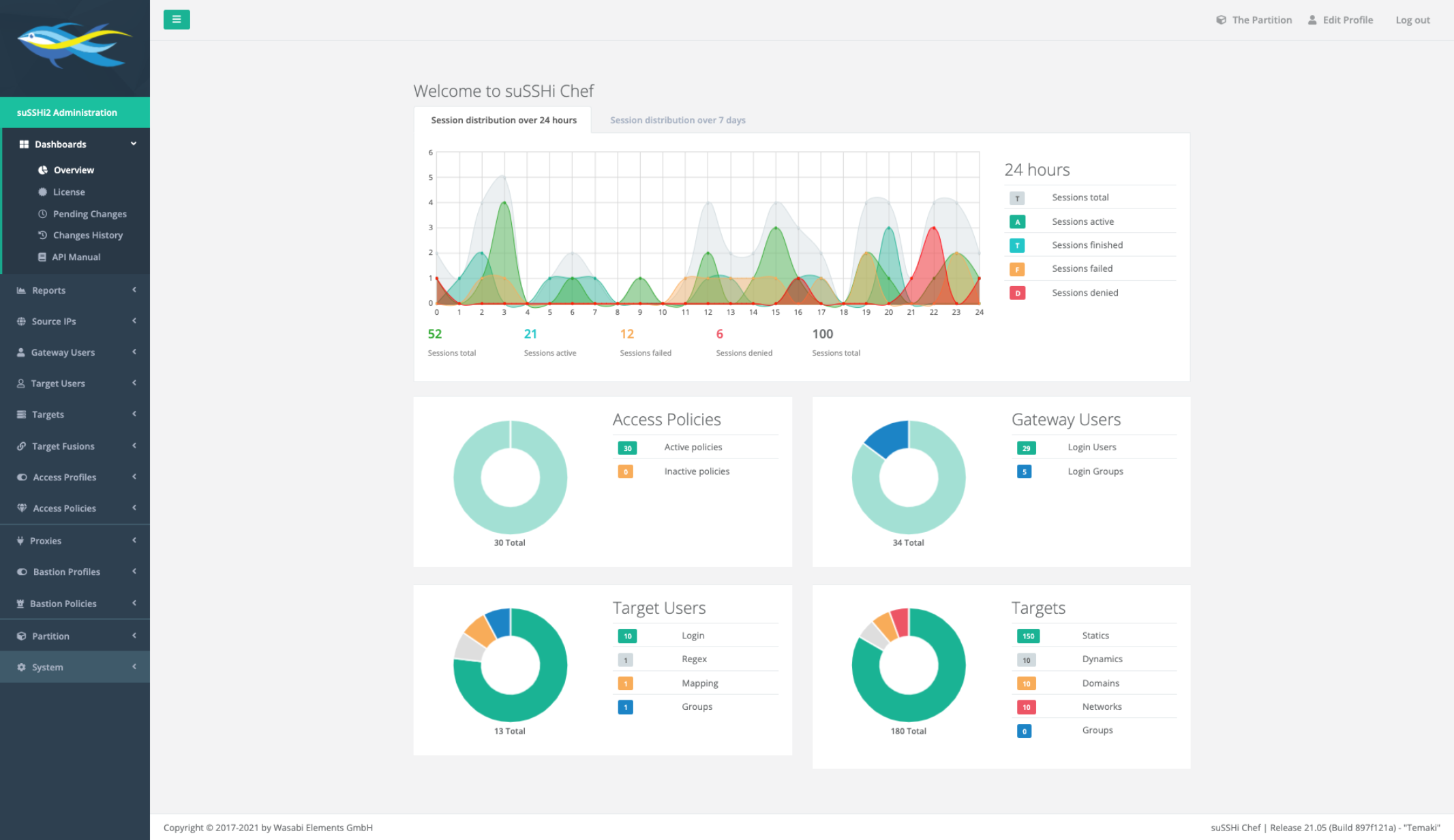
suSSHi Chef comes with sophisticated features as well as advanced integrations and automation options, i.g. a full REST API supports you in gaining full control over all configurations.
Protocol Deep Inspection and Logging
Each session through suSSHi Gateways undergoes a deep packet inspection for all SSH messages within the SSH protocol. Specialised dissectors perform analyzation and protocol aware logging for all sessions and sub-protocols within the RFC standard based SSHv2 protocol suite.
The dissectors allow fine granular control on what is allowed or denied and give you control over protocol specific logging. This includes support for all SSH features such as interactive sessions, file transfers, port forwardings, SSH agent, tunnelings and much more.
Flexible User Mapping
One strengths of suSSHi is the ability of mapping from real users to administrative accounts without loosing any security or control over the target system. This can be further extended with built-in regex and regex-mapping rules to allow easy user mappings with regular expressions patterns.
Flexible Targets
suSSHi supports different kinds of targets to be ready for all situations. Static Targets allow the static mapping to IP addresses with pre-configured (or scanned) host keys - this is the most secure way to configure targets.
Dynamic Targets enable the use of DNS hostnames (FQDN) to identify targets and either have host-keys pre-configured (or scanned) or dynamically learned by the gateway. All dynamically learned host-keys must be accepted and are stored individually per user.
Domain Targets allow the use of DNS domain names to identify targets. Target host-keys are dynamically learned by the gateway, which enables high flexibility in changing targets like in cloud setups.
Network Targets work like Domain Targets, but are based on IPv4 or IPv6 CIDR-addressed networks, if you want to configure targets using IP addresses instead of domain names.
Gateway Performance & Scale-out
Login to a target system via suSSHi adds less than 100ms of delay compared to a direct login. Wire rate performance for active sessions or data copy ensures that the suSSHi Gateway does not act as a productivity limiter in any way. In other words, a user does not recognize the gateway in terms of speed, delay or jitter during session setup, nor during the session.
All session reporting is done asynchronously to avoid blocking the I/O of session processes when handling interactive user or copy sessions which guarantees minimal to none delays and jitter.
To achieve horizontal scaling, additional gateways can easily be added for more parallel sessions as needed. Each gateway operates independently and can even be used in different L3 networks. suSSHi Chef component can also be deployed multiple times for a horizontal scaleout.
IPv4 and IPv6 support
suSSHi has full support for IPv4 and IPv6 and both IP versions can be mixed in various ways.
The IP protocol of the connection to the target server is completely independent of the IP protocol of the connection from the client to the gateway. This for example allows users coming from a pure IPv4 network to connect to servers in an IPv6 deployment and vice versa. Port forwarding can also be combined in both directions.
suSSHi implements a more advanced “Happy Eyeballs” (RFC 6555) that goes further in mixing IPv4 and IPv6 in an administrator configurable way. So you can choose whether you prefer IPv4 or IPv6 addresses and suSSHi will try to connect to the targets in the preferred order. It even traverses lists of IP addresses when DNS resolves multiple IP addresses for a target.